The Legal Fragility of "Standard" Audit Trails
When a signature is challenged in court, a timestamp is not enough. Why most "compliant" audit logs crumble under forensic cross-examination.
In the procurement phase, "Audit Trail" is often just a checkbox. If a vendor claims compliance with ESIGN or eIDAS, the box is ticked, and the team moves on. This is a dangerous oversimplification.
The reality of litigation is far messier than a compliance certificate. When a counterparty claims, "I never signed that," or "My account was hacked," the burden of proof shifts entirely to the party seeking to enforce the contract. In these moments, the difference between a Standard Audit Log and a Forensic Evidence Package becomes the difference between a summary judgment and a dismissed case.
The "I Didn't Sign That" Defense
The most common legal challenge to e-signatures is not technical forgery, but simple repudiation. A signer admits they own the email address but denies taking the action.
In Aerotek, Inc. v. Boyd, the Texas Supreme Court ultimately upheld an e-signature, but only because the platform recorded granular, step-by-step metadata—not just a final "signed" timestamp. The system tracked the creation of a unique user ID, the selection of security questions, and the specific timestamps of viewing each document before signing.
The Failure Point: Many "lightweight" e-signature tools only record the final click. They fail to capture the intent signals:
- Time-on-page: Did the user spend 0.5 seconds or 5 minutes on the page? (Proof of review).
- Sequential Logic: Did they open the email, then view the document, then sign? Or did the signature appear without a "view" event? (Indication of bot activity or API error).
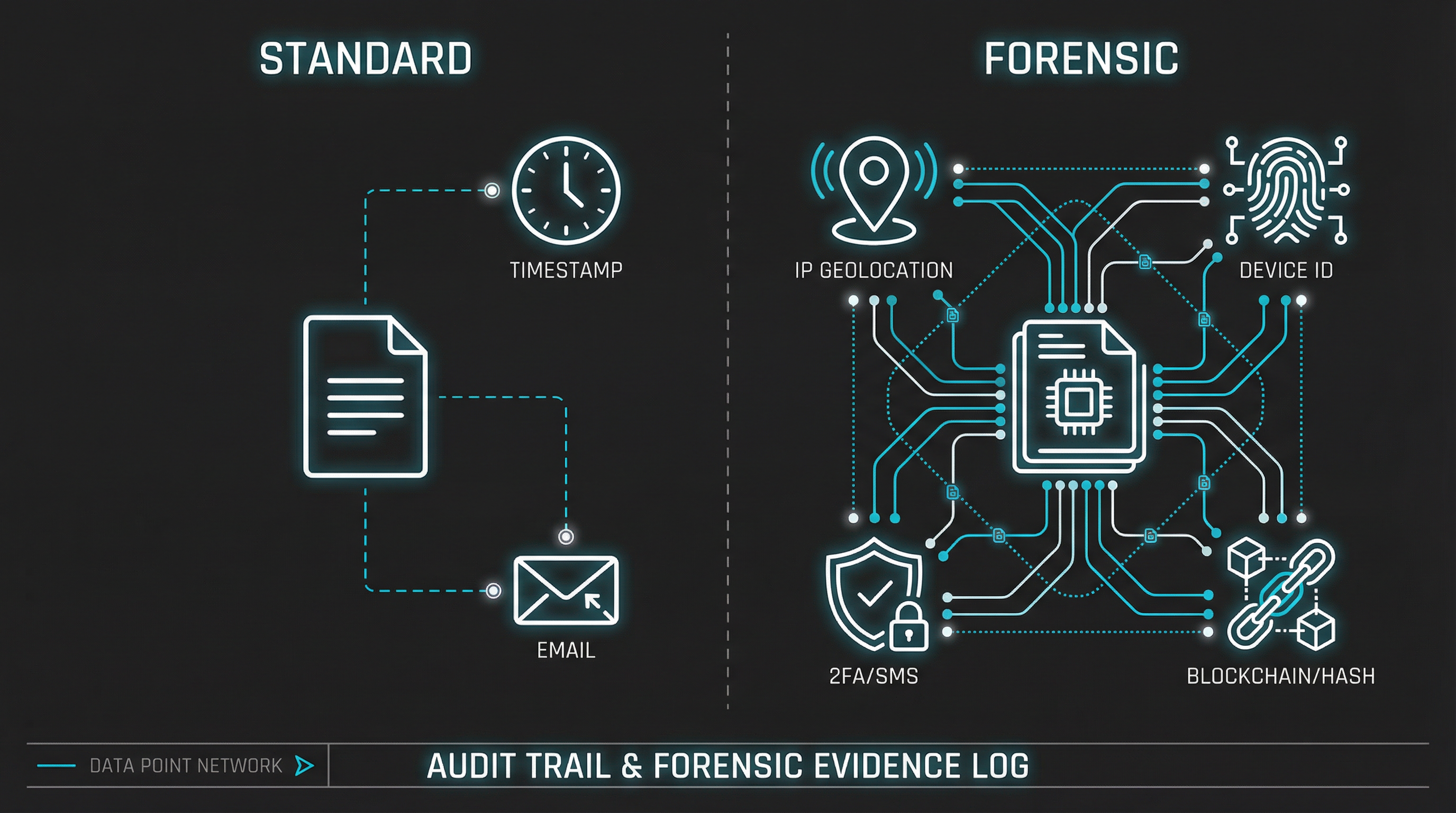
The IP Geolocation Gap
A standard audit trail records an IP address. A forensic log contextualizes it.
Consider a scenario where a contract is signed at 2:00 PM. The audit log shows an IP address belonging to a coffee shop in London. However, the signer can prove they were in a meeting in New York at that time. Without secondary authentication factors—such as SMS verification codes or device fingerprinting—that single IP address becomes exculpatory evidence against the validity of the signature.
Strategic Implication: For high-value transactions, relying on email-based authentication (sending a link to an inbox) is legally fragile. If a user's email is compromised, the "standard" audit trail is worthless.
Metadata Stripping & Long-Term Preservation
Another critical oversight occurs during the export process. When you download a "completed packet" from a SaaS vendor, you often get a flattened PDF.
If you leave the vendor (a risk discussed in our Strategic Guide to Procurement), you lose access to the live, interactive audit log. You are left with a static PDF "Certificate of Completion."
The Risk: In a court case five years later, that static PDF is hearsay. It is a document generated by a third party, not the original digital evidence. Unless you have maintained a "chain of custody"—cryptographically linking the audit log to the document hash at the moment of signing—you may struggle to authenticate the record.
Consultant's Recommendation
When evaluating vendors, ask for a sample "Certificate of Completion" and hand it to your legal counsel. Ask specifically:
- Does it show the "View" event? Proof of access is as important as proof of signing.
- Is the audit log embedded or separate? Embedded logs (within the PDF structure) are harder to separate from the contract.
- What is the vendor's data retention policy? If they purge logs after 7 years, but your contract liability is 10 years, you have a gap.
Do not assume "legally binding" means "court-ready." The former is a marketing claim; the latter is a technical reality.