The Hidden Engineering Tax of "Simple" E-Signature APIs
Vendor documentation promises you can "be up and running in minutes." They show you the request. They rarely show you the recovery logic.
In software procurement, "Ease of Integration" is often judged by the cleanliness of the POST /envelopes example in the documentation. If a developer can send a document in a single curl request, the API is labeled "developer-friendly."
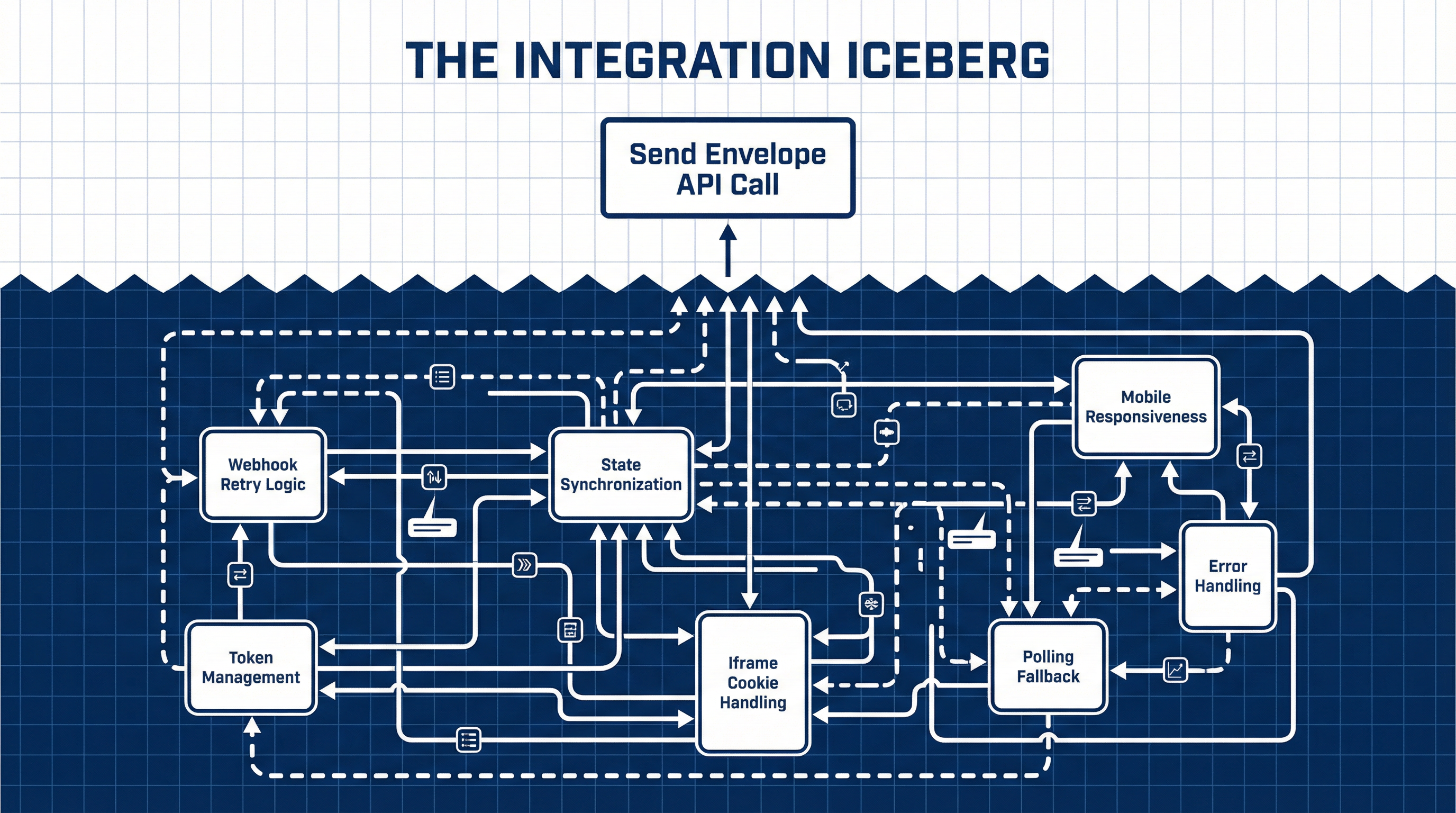
This metric is deceptive. Sending the document is the easy part—it represents perhaps 5% of the total engineering effort. The remaining 95% lies in handling the asynchronous chaos that follows: webhooks that arrive out of order, signers who block third-party cookies, and state mismatches that leave your database saying "Pending" while the contract is already signed.
The Webhook Reliability Trap
Most modern e-signature APIs rely on webhooks to notify your system when a document is viewed or signed. In a perfect world, these events arrive sequentially and instantly. In production, they do not.
A common failure mode occurs when the "Envelope Completed" webhook arrives before the "Recipient Signed" webhook due to network latency or retry queues. If your logic strictly expects state transitions (A → B → C), an out-of-order event (A → C) can cause your integration to reject the update or throw an exception.
The Engineering Tax: You cannot simply "listen" for webhooks. You must build an idempotent event processor that can handle duplicate deliveries, out-of-order arrivals, and silent failures. You also need a fallback polling mechanism (a "sweeper" job) to catch the 1% of events that never arrive, ensuring your platform doesn't leave a deal in limbo just because a webhook timed out.
Embedded Signing vs. Browser Privacy
Product teams often demand "Embedded Signing" (using an iFrame) to keep the user inside their app, rather than redirecting them to the vendor's domain. While this offers a smoother UX, it collides head-on with modern browser privacy protections.
Safari’s Intelligent Tracking Protection (ITP) and similar features in Chrome/Firefox aggressively block third-party cookies inside iFrames. If the e-signature vendor relies on session cookies to authenticate the signer within that iFrame, the session may be silently dropped, leading to infinite loading loops or cryptic "Session Expired" errors for mobile users.
The Engineering Tax: Your team may be forced to implement complex workarounds, such as "storage access API" requests or abandoning the iFrame entirely for a redirect flow on mobile devices. This bifurcation doubles the testing surface area.
The "Signed but Not Ready" Race Condition
Another subtle issue arises immediately after the signature. Your system receives the "Signed" webhook and immediately attempts to download the PDF to store it in your own records.
However, many providers have a latency gap between the event and the artifact. The database record is updated, but the final PDF (with the seal applied) is still being generated in an async worker queue. If your code requests the document 50ms after the webhook, you might get a 404 error or a corrupt file.
As discussed in our Strategic Guide to Procurement, evaluating a vendor isn't just about their feature list—it's about the maturity of their infrastructure. A robust API will either block the download request until the file is ready or provide a specific "Document Ready" event separate from the "Signing Completed" event.
Consultant's Recommendation
When your engineering team estimates the integration effort, ask them to multiply their initial "happy path" estimate by three. Specifically, ensure they have accounted for:
- Reconciliation Jobs: A nightly script that compares the vendor's state with your database to catch missed webhooks.
- Environment Parity: Does the vendor's sandbox behave exactly like production? (Rate limits and latency often differ wildly).
- Error Taxonomy: Does the API return generic
500 Internal Server Errorfor everything, or specific codes for "Invalid Email" vs. "System Down"?
True "simplicity" in an API is not about how few lines of code it takes to start, but how few lines of code it takes to handle failure.